For the fourth installment of our personal security guides, we are covering how to secure your computer.
This includes current versions of Mac (Sierra) and Windows (10). In a future post, we will cover some mitigation protocols for outdated operating systems.
Note: I personally do not use Windows for privacy reasons. If you use Windows 10, I recommend looking into ways to mitigate the privacy issues. We do not cover privacy much in this article. If there is interest, we can revisit the topic in a future article.
Securing your personal computer is an important task for website owners to undertake because it can be a vector that causes your website to become infected. A good security guide for websites will mention scanning your computer for malware if your website has been hacked. Malware has been known to jump from an infected user’s computer through text editors and FTP clients. Fostering good habits throughout your digital life helps strengthen your overall security posture.
0. Reformat (optional)
If the computer isn’t new, it is a good idea to reformat so you are starting with a freshly installed operating system. This ensures your computer is completely free of any malware and old data that might slow things down.
After reformatting you can easily reinstall your favorite programs using MacApps or Ninite for Windows.
Mac:
- Open the Disk Utility.
- Select your startup disk from the list on the left, and then click the Erase tab.
- From the Format pop-up menu, select Mac OS Extended (Journaled).
- Name your disk and then click Erase.
Windows:
- Open your Windows Settings.
- Select Update & security.
- Click Recovery in the left pane.
- Click Get started under Reset this PC.
- Click either Keep my files or Remove everything.
After reinstalling your operating system, be sure to keep your software up to date. On Mac you can open the App Store and check for updates. To keep programs up to date on Windows I would recommend using Personal Software Inspector or Filehippo Update Checker.
1. Settings
Most of this guide will include similar advice for securing both Mac, via System Preferences, and Windows, via Control Panel.
i. Log in & Timeout
When you log in to your computer, use a strong password and change it every six months.
Ideally, the screensaver should come up after a short period of inactivity (2 minutes or less) and ask for the password.
Mac:
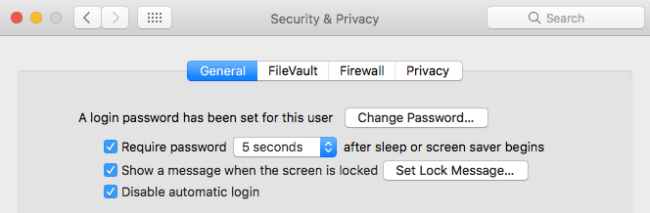
- Open the Security & Privacy system preferences.
- Change your password if needed.
- Check the box to Require password and select a short length of time from the drop-down menu.
- If using a screen saver, open the Desktop & Screensaver system preferences.
- Click the Screen Saver tab and select a length of time for it to begin from the Start after drop-down menu.
Windows:
- Open your Settings and click Accounts.
- Open your Sign-in options and click the Change button to change your password.
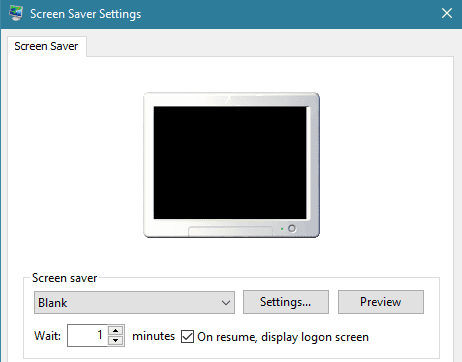
- Click Home to go back to Settings, click Personalization and click Lock Screen.
- Select Screen saver settings.
- Select a short length of time from the Wait menu.
- Check the box On resume, display logon screen.
ii. Remove Unwanted Programs
You should remove all unused programs and bloatware from your computer. It’s important to do this because these programs can have privacy issues. Just like with removing unused plugins, modules, and themes on your website – if something isn’t installed, it can’t be used as a possible way to infect your machine.
If you aren’t sure of the purpose of a specific application, do some research online to confirm whether it is a necessary application or something you can safely remove.
I recommend removing Adobe Flash Player and Java. These applications have a history of security issues, and modern browsers can handle Flash content natively.
You can replace Adobe Reader with something like Foxit Reader. The best option is to not have a PDF reader installed and open them online using Zoho Viewer for example. You could use Google Docs, but I try to avoid Google products due to issues with privacy.
For replacing Word/PowerPoint/Excel etc., I would recommend OpenOffice or LibreOffice instead, which are both less targeted and open source. This helps prevent the spread of malware that takes advantage of vulnerabilities in Microsoft Office products.
Mac:
- Open the Applications folder.
- Delete any applications you do not need.
Windows:
- Open the Add/Remove Programs panel.
- Uninstall any applications you do not need.
- If you have issues uninstalling a particular application, try Revo Uninstaller which removes all Windows registry entries and orphaned files related to the program.
iv. User Accounts
As we are big on the principle of least privilege for website related things, make sure you are using a standard account for day-to-day things and not an Administrator account.
You may want to enable a Guest account for anyone other than yourself who needs access to your computer.
iv. Built-In Security
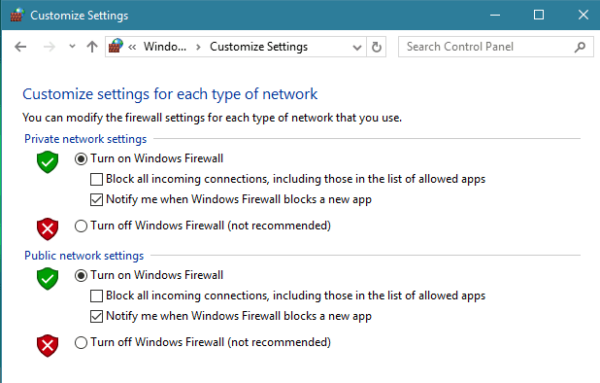
You should be sure to enable the default firewall in your Network settings on both Mac and Windows. For any network you connect to, make sure to select the Public option as that blocks incoming connections by default.
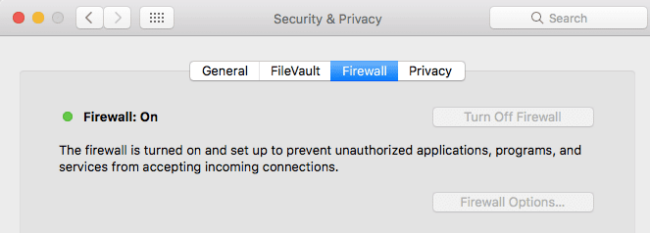
On Mac, I use full disk encryption (FDE) with FileVault (available under your Security & Privacy settings).
2. Software Solutions
This section lists some recommended software to keep your machine clean and optimized.
i. Backup
Mac: I don’t use iCloud because the files are accessible by Apple and have known issues regarding privacy. I use full disk encryption with FileVault and then a separate container with VeraCrypt for all of my files. I put my KeePass file in my VeraCrypt container and copy that manually to two flash drives that I keep in separate locations once a week. I then upload the VeraCrypt encrypted file container to SpiderOak ONE to have a backup online in case I lost my computer and two flash drives for some reason.
Windows: Make sure you encrypt the disk with Bitlocker. Another option you can look into is VeraCrypt. For backups I would recommend SpiderOak.
ii. AntiVirus
It’s important to have a good antivirus to scan your system with regularly. Some also offer active protection, which helps prevent malicious downloads by scanning all downloads and putting anything suspicious into quarantine.
I do a weekly scan with Malwarebytes Anti-malware to be safe. Then I do a monthly scan with Avast.
Both are available on both Mac and Windows, however there are plenty of other vendors who offer respectable antivirus applications.
Mac: If you are not comfortable with advanced firewall alerts described in the next section, you should at least have an antivirus running in the background to detect issues in real-time.
Windows: It’s an absolute necessity to run an antivirus program that includes active protection, as the majority of infections still target this operating system.
iii. Firewall
A firewall will monitor internet traffic being sent and received from your computer. This allows real-time blocking of malicious traffic. All firewalls function this way in order to protect an endpoint from becoming hacked. The Sucuri Firewall, for example, blocks malicious traffic to your website.
The alerts can be quite technical, but with some research and patience, the learning curve is worth it – far better than any antivirus solution in my opinion. If you can understand the alerts, use them carefully so that you pick the appropriate response when asked to allow or deny a connection.
Note: If you aren’t very technical and would likely allow everything for convenience, it is better to use a good antivirus that can do this for you instead.
Mac: I use Little Snitch which is a very good solution for monitoring all outgoing network connections. For monitoring access to files, I use Little Flocker.
Windows: If you are looking for a bit more control or advanced firewall the free Comodo firewall is a good option.
iv. Encryption
If your computer is ever stolen, encryption makes sure your data is not at risk (assuming you have a strong password as described in the first section).
Mac: In addition to the built-in FileVault, I also create a separate container with VeraCrypt for my own files is so that if the computer is on and your data is not encrypted by full disk encryption then the VeraCrypt file container will still protect your files.
Windows: I recommend you encrypt the disk with Bitlocker or VeraCrypt.
iv. Other Recommendations
I use a virtual machine for day-to-day, as this allows you to contain your activity. This is especially useful when handling suspicious content or questionable sites you want to visit. VirtualBox is a good free option.
You can also use an optimizer like CCleaner or Bleachbit to clean up unnecessary files. This just keeps things running smoothly and can speed up your system by removing unnecessary data and orphaned files.
Using a VPN is also a great option for surfing the internet privately, as this masks your network so it is not easy to identify you. I recommend ProtonVPN, which is the only one I use.
Conclusion
This is not an exhaustive post by any means. We wanted to make sure it was easily digestible and action-oriented. There is plenty of good sources online and we encourage you to continue your education as the cybersecurity space changes frequently. For more information you may want to check out our guides to securing your browser, home network, and online accounts.
You can also look into additional privacy settings as there are many options. For example, I recommend covering up your webcam. Malware has been known to take pictures and video without the user’s knowledge, which is an unsettling thought.
Look forward to our next post in the series which will cover my approach to mobile device security.
If you have recommendations on how to improve this article, please let us know by tweeting us @SucuriSecurity, or you can email us at info@sucuri.net.










3 comments
Good overview! A neat little program I use on MacOS is AppCleaner, it removes the various system files associated with programs that typically don’t get removed during normal uninstall (1.ii.)
Thanks a lot Caleb !
Your article has been of great help to my computer security.
If they do not use the computer for very special things like games it would also be highly recommended that they install Linux (Ubuntu, Debian, Fedora….) that is free and more secure than Windows
Comments are closed.