Question: How should a website owner differentiate between firewalls? What do they do?
The term “firewall” is not new. It is common terminology in the world of technology and security, and possibly common enough that even non-technical people have a basic understanding of what a firewall is. Its meaning actually extends beyond security. The brick walls that divide different sections of a building are called firewalls. We even have firewalls in our cars. They’re the metal wall that separates the engine and passenger compartments. The term transcends multiple industries because it’s so indicative to what is happening. Regardless of industry, the core function has always been to separate two different spaces. Those spaces have always had two core purposes:
- To keep something out
- To keep something in
The term is used so interchangeably in security discussion, especially website security, that it can be confusing. There are many kinds of firewall, such as our own cloud WAF (website application firewall). Many attribute firewalls to functioning the same, this is false. When it comes to websites / servers / networks they fall into three distinct domains that I feel are important to differentiate.
There are three categories to account for when thinking about Firewalls:
- Network
- Local
- Application
Network Firewalls
In large organizations you’ll often see the deployment of large-scale network firewalls designed to protect an organization’s environment from unauthorized access into a specific environment.
Network Firewalls are what we’re most familiar with. You can find them in our home routers, protecting our trusted zone (home network) from an untrusted zone (the internet). In large organizations you’ll see similar configurations, but with additional firewalls as well that isolate different parts of a network, protecting their network assets (trusted zones).
These firewalls are designed to look at network connection attempts to various network ports, as well as analyze incoming packets and their associated metadata. Based on rules, the firewall then determines what is and isn’t allowed into the environment they are protecting.
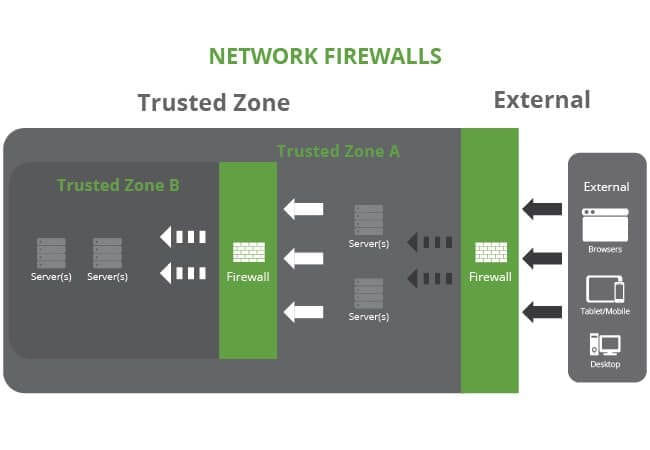
In many instances, these network firewalls come in the form of hardware or software that looks at the network as a whole. Firewalls at the perimeter of a network that sit in front of web servers, by design, allow port 80 and 443 which are specific HTTP/HTTPS (web) traffic. If the network firewall sits in front of a mail server, it allows port 25 which supports SMTP. The list goes on, based on the specific applications your enviornments has to host.
When thinking about your website, this is what your host is often referring to when they say they employ specific firewalls onto their network to keep you safe. The problem however is by default web traffic has to be allowed through the network.
Note: There are some network firewalls that allow configurations to focus on web traffic specifically.
Local Firewalls
Local Firewalls are also designed to protect trusted from untrusted environments, but function at a different level. They are focused on a specific environment, whether that is a server or your desktop. You will find local firewalls on all of your devices. Every device may have it’s own configuration and access requirement, and your local environment becomes it’s own trusted environment.
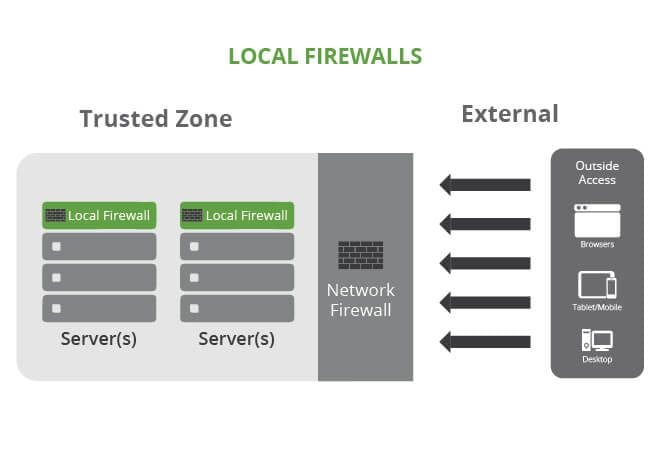
When working with your website host, your access to the local firewall might be limited depending on the type of configuration you have (i.e., Shared, VPS, Dedicated or Managed Host). Most hosts though, regardless of your configuration, should be leveraging both network and local firewalls across their entire network. Their network firewalls protect the perimeter, and the local firewalls protect the specific assets within the perimeter. Similar to the network firewall however, the local firewalls have little to do with the security of your website.
The biggest mistake any organization can make is to assume that because something is within the network it’s safe.
Application Firewalls
Application firewalls, while similar in design to Local and Network firewalls, are complementary technologies to existing security deployments. Application firewalls move beyond the metadata of the packets being transferred at the network level and focus on the actual data in transfer. They are designed to understand the type of data allowed within specific protocols -think SMTP or HTTP. There are specific firewalls for different applications, like email or website firewalls.
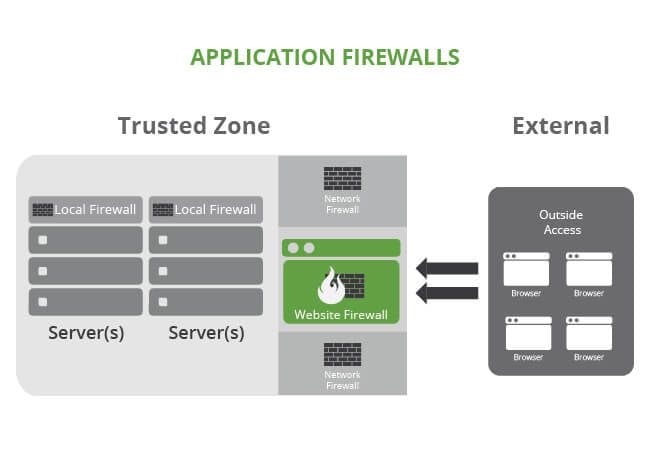
Application firewalls can be hybrid deployments. You can find them at the local or network level. It depends on how the organization has them configured. The question website owners should be asking their hosts is how do they handle specific threats to their website. Some hosts deploy application firewalls, some are proprietary (built in-house), others leverage open-source technologies like ModSecurity. Few deploy cloud-based firewalls (e.g., Sucuri Firewall).
Websites Need Application Firewalls
The threat landscape for websites is evolving at an alarming rate, so much so that it’s making it impractical for most system administrators to keep up. It’s not enough to deploy network and local firewalls anymore. While some can be tuned to account for web traffic many are ineffective when focusing on web-specific traffic. Especially at the rate of change we’re seeing around the anatomy of website-based attacks.
The most effective Web Application Firewall (WAF) will provide your company the peace of mind it requires in knowing that its online presence is being taken care of 24/7 with little interaction from your team. The most common misconception I hear from website owners is that this is the type of security they expect from their host but it’s not. It’s why organizations like Sucuri exist.
Website hosts have one focus. To make sure your website is accessible. Security though, is a domain within itself requiring countless hours of research and development. The same can be said for performance, it’s why Content Distribution Networks (CDN) exist. Most of today’s hosts have a deployment of ModSecurity (comparable technology) deployed within their environment but lack the team or resources to stay ahead of the existing threats, let alone the emerging ones. Their shortcoming will always be in its maintenance.
A host’s concern around security will always be restricted to how much it impacts their margins or brand, not how much it impacts the website owner. Website compromises become acceptable collateral when compared to the overall network, will your website be that collateral damage?










1 comment
i am using the comodo firewall – works quite well !!!
Comments are closed.