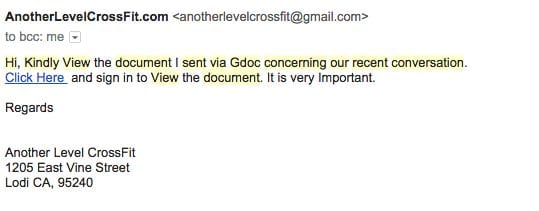
We get thousands of spam and phishing emails daily. We use good spam filters (along with Gmail) and that greatly reduces the noise in our inbox. Today though, one slipped through the crack and showed up in my personal inbox:
As I went to mark the email as Spam, I decided to hover over the link. I saw that it was pointing to a compromised WordPress website and the phishing page was hidden inside wp-includes: httx://www.uncannyhawaii. com/wp-includes/js/lexx/loading.htm.
We detect and remediate thousands of compromised WordPress websites every month, most are used for spam and malware distribution; and many often demonstrate some sign of Phishing abuse. We have talked about Phishing before as well, it is always hard to detect remotely because the attacker is able to hide the payload anywhere in the site. They hide it in sub-folders that are not linked from the main pages. This causes our SiteCheck scanner to overlook them, making it impossible to see. We rely heavily on our server-side scanning to detect Phishing pages, but prospective clients would not have access to it.
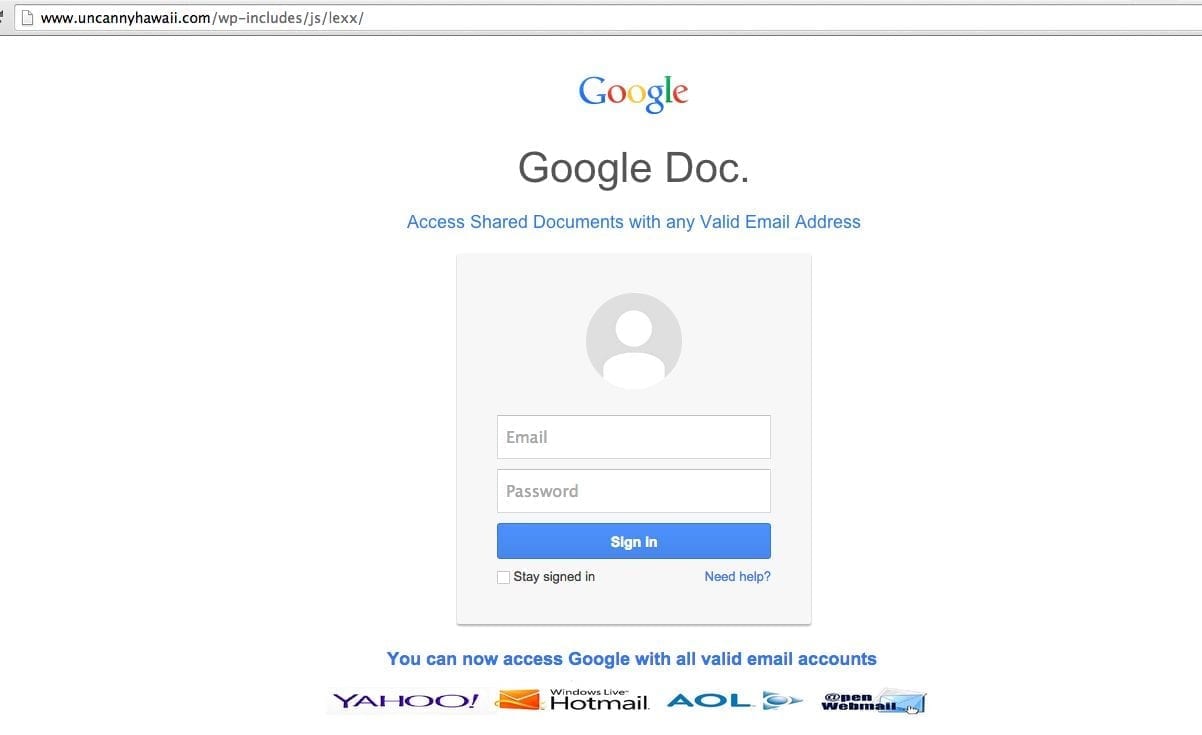
This prompted further investigation, mostly because I was curious of what I would find. As soon as you click on the phishing link you see a fake Gmail login page, just like this one:
This is not uncommon, we have seen this before. The attacker records the users username and password, send it back to the Command and Control (C&C) node and responds to the browser with a not-available page. The user is often non the wiser, assumes there is a time out in the service and goes about their business. Once they realize what has happened, there is often little they can do, the compromise has occurred.
This user name / password combination makes it’s way onto a user / password list that can later be sold or attacked by the hacker.
The kicker to this story is that the the website owner is likely unaware of how their website is being abused and misused. This is in all too common trend these days. Attackers have an arsenal of options once they gain entry to your website, what you see is often only 10% of the problem.
To illustrate the impact and correlation between Phishing attacks and more traditional Malware attacks we can take a quick look at the Google Transparency report:
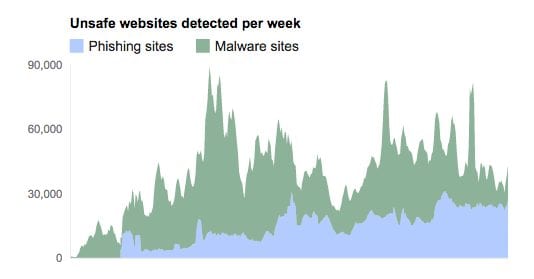
What you see in this report is a gradual increase in daily detection of Phishing pages by the Google Safe Browsing team. In 2008 there were approximately 3,000 Phishing pages detected a day, today you’re looking at 23,000 plus. The problem is growing exponentially each year.
Not a unique Story
As is often the case when I find something interesting, I rallied the research team for some hunting. We spent some more time going through our spam folders, in an effort to compile a list of WordPress specific websites that had been compromised.
Within minutes, we were able to find hundreds of compromised WordPress sites being used, here is a very small subset of the ones we found:
httx://ampconstrucciones.com.co/wp-includes/ID3/UK/clients/home/
httx://mediapenjas.com/wp-includes/js/jcrop/spakde/index.html
httx://www.jacks-music.co.uk/wp-includes/rer/
httx://www.casadobarro.pt/wp-admin/user/accounts.google/GoogledocsSecure_files/
httx://yellowbeautifulpearl.com/wp-includes/personal/log1n-jsp.html
httx://educationfront.com/wp-admin/maint/sparlk/index.htm
httx://alpinestarholdings.com/wp-includes/wellsfargo/update.htm
httx://www.odorizantes.com.br/wp-content/themes/new.file.open.drive/onenewdrivecloudefile
httx://www.velhomonge.com.br/wp-includes/images/smilies/link1140/
httx://oia.unsyiah.ac.id/wp-includes/js/fr/PayPal/fr/
httx://www.specialtributes.com/wp-content/themes/google/
httx://cayyoluevdenevenakliyat.com/wp-includes/js/tinymce/plugins/
httx://cjcollegeprep.org/wp-content/themes/news/doc2014/
httx://www.heal-group.com/wp-content/plugins/wpclone/lib/images/alibaba/aliB.htm
httx://www.ancacunescu.ro/wp-content/plugins/akismet/views/
httx://www.peninsulachiro.ca/wp-includes/WW-AA/FedEx/
httx://www.escueladeruso.com/wp-includes/mrtp/
httx://hotwheelrollerderby.co.uk/wp-content/gallery/media/dynamic/file1/file1/googledoc.html
httx://www.upsd.org.tr/wp-content/plugins/akismet/royalbank/
httx://www.ariane-agencement.fr/wp-content/plugins/ss/nn/266e907b2cee6886920b4115b1f6683a/
httx://hotel-orbita.com/wp-includes/css/css/
httx://www.goedangfurniture.com/wp-admin/online.wellsfargo.com/account/verify/
httx://zapwater.com/wp-content/themes/Google2014/link/
httx://www.cafetoalmacen.com/wp-content/uploads/2014/04/wash/
httx://www.greekjourney.com/blog/wp-content/plugins/plugins/geo-mashup-1.4.1/wp-content/
httx://dimensi-tour.com/wp/wp-content/themes/zippy/Constantine.php
httx://www.3designcenter.com/blog/wp-includes/js/other/
httx://www.thevapour.net/wp-content/themes/twentytwelve/standardcino3/
Please don’t click on any of these without JavaScript/Flash and Java disabled, but they are all used as fake login pages for eBay, Paypal, Fedex, Halifax, Alibaba and a few other financial institutions.
As you can see, the attackers are able to somehow compromise these sites and hide Phishing directories in a variety of locations inside wp-includes and wp-content.
How are these sites getting hacked?
That’s always the first question that people ask us. We analyzed all the WordPress sites we found and 73% of them were updated (either running 3.9.2 or 4.0).
The other 20+% were running some old versions of WordPress (some still on the 2.x branch).
So the question goes, if these sites are updated, how are they still getting hacked? We obviously didn’t have server or log access to do a full audit, and the sites seem to be located on different hosting providers.
So we put one of our researchers to work, Joseph Herbrandson. His goal was simple, find the common denominator. What he found was that a very high percentage of them were running a vulnerable WordPress plugin, whether it suffered from Remote Command Execution, SQL Injection or any of the variety of software vulnerabilities we love to chat about. They included out of date versions of contact-form-plugin, feed<, contact-form-7 and the list goes on.
While it’s impossible to confirm, it would seem that the point of entry is most likely attributed to the exploitation of software vulnerabilities (granted without access we might never know). This would leave us to believe that attackers are employing their exploit arsenal against known vulnerabilities in the hopes that something sticks, and when they do, they go about doing their business to gain access to the environment.
Phishing Kits
Some of the attackers were not very careful and left their tools behind (in zip files). We are able to find a couple of email addresses being used to receive the credentials:
chongwale123@gmail.com
ungofullz@gmail.com
If you see anything in your mail logs to (or from them), you know someone fell victim to the phishing lure.
Detecting Phishing
As we stated in the beginning, detecting phishing is very hard to do remotely via a website scanner. As you can see in some of the examples, the phishing is hidden inside directories like “wp-content/uploads/2014/04/wash/” that are not linked on the main site. That’s why if you have a phishing, our free SiteCheck scanner will not flag it.
We leverage server-side scanning for our clients, where we go through each file and directory to try to identify hidden phishing, backdoors and other types of injections that are not linked within the site. That way we do not have to rely on 3rd party blacklists or email honeypots to see if a site is being exploited. Our Website Firewall also blocks access to phishing files and prevent them from being used.







8 comments
I have noticed the same use of WordPress sites in the past, even went a far as emailing the owner of a site to let them know – never got a response. We would all benefit from having those sites cleaned up. As you mentioned if 73% were updated then someone cares enough about them to keep them updated. Unless of course the hacker is patching them to stop others from getting in.
It could also be a good revenue steam for a company like Sucuri. If you had your email honeypots scan for WordPress directories in the URL and then auto generated an email to the site owner and the hosting company to let them know about the issue. Maybe too SPAM like, but if this was my site I would want to know.
(pt_BR) OK Sucuri, posso então entender duas coisas então:
01 – O Sucuri WordPress Plugin agenda o Scan apenas da Página Inicial do Site?
02 – Se algum Scan a partir do Site é solicitado, apenas a Página solicitada é Scaneada? Dessa forma a sua ferramenta não analisa “toda” a hierarquia dos Sites?
(Google Translate, sorry)
OK Sucuri, then I can understand two things then:
01 – The Sucuri WordPress Plugin schedule the scan only the Home Site?
02 – If a Scan from the Site is requested, only the requested page is scanned? That way your tool does not analyze “all” the hierarchy of sites?
(pt_BR) Uma solução para esta “detecção falha” não poderia ser a integração (API) com outros plugins que realizam esse Scan Profundo?
Por exemplo: Eu uso esta combinação de plugins/serviços (todos gratuitos) para “lacrar” meus Sites/Blogs;
– Gestor de DNS + Anti DDoS + Cache: CloudFlare;
– Firewall : CloudFlare + Wordfence + CloudFlare Threat Management
– Scanner Interno Profundo: Wordfence Security
– Hardening + Scan Externo: Sucuri Security
Não seria o caso de integrar o Sucuri com o Wordfence? ou Wordfence com o VirusToral ou outra ferramenta especializada? O Plugin iThemes Security (antigo Better WP Security) desde a versão 4.4.11 tem a opção do cliente colocar a sua API Gratuita do VirusTotal para comparar os arquivos scaneados.
Obs: O que acham da minha combinação de plugins/serviços para Segurança?
(Google Translate, sorry)
One solution to this “fault detection” could not be integration (API) with other plugins that do this Deep Scan?
For example: I use this combination of plugins / services (all free) to “seal” My Sites / Blogs;
– DNS Manager + Anti DDoS +Cache: CloudFlare;
– Firewall: CloudFlare + Wordfence + CloudFlare Threat Management
– Internal Deep Scan: Wordfence Security
– Hardening + External Scan: Sucuri Security
It would not be the case for integrating Python with Wordfence? or Wordfence with VirusToral or other specialized tool? The iThemes Security Plugin (formerly Better WP Security) since version 4.4.11 has the option of putting your customer is free VirusTotal API to compare the scanned files.
PS: What do you think of my combination of plugins / services for Security?
Note that the Free version of CloudFlare does not include a firewall (just the CDN for performance). But yes, when we mix the external scanning and other security tools you can detect it pretty well.
Hello Daniel, I’m sorry for not explaining
Free CloudFlare really does not have the Firewall, only the CDN, Basic AntiDDoS, AntiSPAM, SSL and now (since the beginning of the month).
https://www.cloudflare.com/plans
In the case I referred to the WordFence Free Firewall: The WordFence integrates with CloudFlare Plugin with the “CloudFlare Threat Management” using the CloudFlare API. https://wordpress.org/plugins/cloudflare-threat-management
Recalling that one of the Firewall (paid) options for WP is the CloudProxy Sucuri own (http://cloudproxy.sucuri.net)
Thanks for this, I think I will pass this on to my clients. Most of them think along the lines of “my website is so small, why would anyone want to break in” or “I can always just go back to one of my backups”. Not many seem to realize that you, as a website owner, have the shared responsibility of keeping the web safe. That means limiting the possibilities of harmful access to your website and making sure your website can’t be used for purposes as described in this article. It’s not just about you as an individual (website), you put others at risk as well if you don’t take care of your security.
Very well said!
Why thank you! 🙂
Comments are closed.